How can airline CTI teams use active defense and decoy data to neutralize Scattered Spider loyalty fraud campaigns and detect Evilginx2 reverse proxies?
That question reflects a growing reality inside airline security teams. Account takeover is no longer a downstream fraud event. It is an access-layer problem driven by adversaries who specialize in impersonation, reverse proxies, and rapid monetization of loyalty accounts.
For Cyber Threat Intelligence teams, the mission is not to clean up after fraud. It is to disrupt adversary capability early, attribute campaigns accurately, and break the kill chain before customer harm occurs.
This article reframes airline ATO through a CTI lens, showing why reactive takedowns fail, how access-based attacks actually unfold, and how decoy data enables preemptive, active defense.
Why airline ATO is a CTI problem, not just a fraud issue
Airline accounts are high-value targets because a single compromise unlocks multiple monetization paths. Loyalty balances can be drained or resold, itineraries can be manipulated, refunds abused, and partner ecosystems accessed.
From an attacker’s perspective, airlines offer three advantages:
- High asset liquidity through loyalty programs
- Legitimate variability in customer behavior that hides abuse
- Operational sensitivity that discourages aggressive controls
Traditional fraud tooling focuses on transactions. CTI teams need to focus earlier, at the access and impersonation layers where attacker workflows begin.
Evil twin and reverse proxy attacks in airline campaigns
Modern airline ATO campaigns commonly rely on evil twin or adversary-in-the-middle techniques. Reverse proxy frameworks such as Evilginx2 proxy the legitimate airline login flow, capturing credentials and session tokens in real time.
This matters because MFA does not fail. The authenticated session is relayed through the proxy.
Once the attacker captures a valid session token, they can replay it directly against the airline site, appearing indistinguishable from the legitimate user. From the platform’s perspective, authentication already succeeded.
Access-based impersonation is effective because it:
- Exploits brand trust and airline-specific urgency
- Operates entirely outside the airline perimeter
- Converts directly into valid sessions rather than stolen passwords
For CTI teams, this shifts detection away from credential compromise and toward session integrity and behavior sequencing.
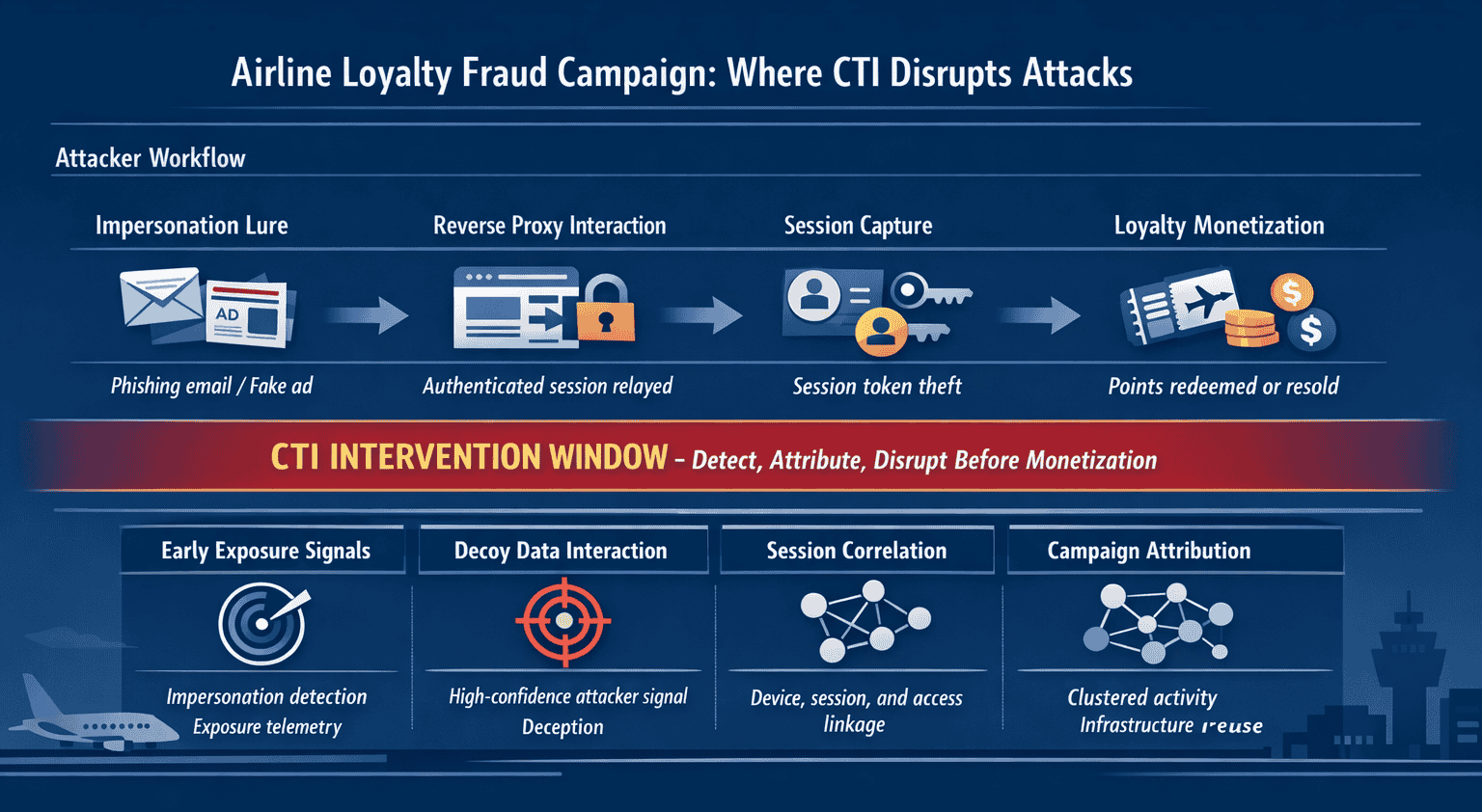
From initial access to loyalty fraud: the real attack chain
Airline ATO is rarely a single action. It is a compressed sequence designed to monetize access quickly and quietly.
A typical chain looks like this:
- Impersonation and access capture
A customer interacts with an airline lookalike site or proxy. Credentials and tokens are harvested. - Session establishment
The attacker replays the session against the real airline site, often from a different device or network. - Account hardening
Recovery factors are changed. Email addresses, phone numbers, or MFA settings are modified to lock out the real user.
Detection and disruption must occur before this stage, once recovery controls are changed, prevention becomes significantly harder.
- Monetization
Loyalty points are redeemed, tickets booked, or refunds requested. In some cases, attackers act as informal travel brokers, reselling flights purchased with stolen points. - Scale and repeat
Infrastructure, lures, and workflows are reused across multiple victims.
If CTI visibility begins at step four, the attacker has already succeeded.
The diagram below shows how airline loyalty fraud campaigns unfold in practice and where CTI teams can intervene before monetization.
Why airlines and customers miss the access layer
Most airline customers never realize they interacted with an impersonation site. The experience looks legitimate, and the damage often surfaces days later as a missing balance or altered booking.
Internally, security teams face two structural blind spots:
- Off-perimeter activity. Traditional monitoring cannot see what happens on attacker-controlled domains.
- High behavioral noise. Travel naturally produces logins from new locations, devices, and networks, reducing the signal quality of anomaly-based alerts.
Takedown services provide eventual domain removal, but that does not help identify victims or stop attacks already in motion.
For CTI teams, a domain discovered after damage occurs is not intelligence. It is evidence of a missed detection opportunity.
The CTI pivot: active defense with decoy data
Active defense does not mean hacking back. It means shaping attacker outcomes.
Decoy data is central to that shift. When deployed correctly, it turns impersonation attempts into intelligence and disruption points.
When used in impersonation and credential-harvesting flows, decoy data enables three CTI advantages.
Attribution through high-confidence signals
Decoy identifiers, credentials, or fields that only appear in attacker-controlled interactions allow analysts to cluster activity. Reuse patterns across sessions, devices, and infrastructure help link incidents to organized campaigns rather than treating them as isolated fraud cases.
Kill chain disruption
When attackers attempt to monetize decoy data, workflows fail. Redemptions break, bookings collapse, and operational friction increases. Attackers are forced to retool, increasing cost and dwell time.
Faster detection with less noise
Decoy interaction is intentional and rare. It generates high-confidence alerts that cut through the noise created by legitimate travel behavior.
For CTI teams, this turns impersonation from an external blind spot into a measurable, actionable signal.
Detecting access-based compromise in real time
Airline ATO prevention depends on timing. Loyalty abuse and booking fraud can occur minutes after access is gained.
High-signal sequences CTI teams should prioritize include:
- New device or network followed immediately by loyalty redemption
- Recovery factor changes shortly after login from an unusual context
- Password resets paired with refund or passenger name changes
- Multiple accounts accessed from the same device fingerprint
These sequences indicate access misuse, not benign customer behavior. Routing high-confidence signals into IAM and fraud systems enables step-up authentication, temporary holds, or session invalidation without blanket friction.
Why traditional tools struggle with these attacks
Legacy defenses were not designed for adversary-in-the-middle campaigns.
Endpoint tools do not see browser-based session replay.
Post-login fraud controls act after access is established.
MFA confirms identity but does not protect session tokens.
Takedown services act after impersonation sites are live and victims are already exposed.
The result is a reactive posture focused on reimbursement and remediation rather than disruption.
CTI teams close this gap by demanding visibility into impersonation activity, live sessions, and attacker infrastructure patterns, not just fraud outcomes.
From visibility to response: what changes for CTI teams
When impersonation and access telemetry is available in real time, CTI teams can shift from alert consumption to adversary containment.
That visibility supports:
- Rapid victim identification and targeted response
- Correlation of incidents across accounts and campaigns
- Evidence-based attribution and reporting
- Measurable reductions in time to detect and respond
Instead of asking how fraud occurred, teams can ask which attacker workflows were interrupted and which need further disruption.
Preparing for the next wave of access-driven attacks
Access-based ATO and proxy-driven impersonation will continue to evolve because they work. Airlines should expect faster attack cycles, more convincing lures, and tighter coupling between access capture and monetization.
CTI teams should focus on:
- Treating impersonation as a primary intelligence source
- Using decoy data to create attacker friction and signal
- Measuring time to detect and respond, not just loss
- Integrating real-time signals into IAM, fraud, and SOC workflows
The objective is not perfect prevention. It is sustained disruption that makes airline campaigns expensive, unreliable, and unattractive to run.
How airline CTI teams stop access-based ATO attacks
Airline CTI teams can use active defense and decoy data to detect impersonation early, identify compromised sessions, and disrupt Scattered Spider loyalty fraud campaigns. By disrupting campaigns that rely on tools such as Evilginx2 before monetization, and breaking attacker workflows before monetization, CTI teams reduce dwell time and the window of exposure, while disrupting account takeover before monetization.
Book a product tour and discover why global airlines implement Memcyco as part of their pivot to preemptive cybersecurity. We’ll show you exactly how Memcyco’s decoy credentials work, and offer estimates on ATO and cost-reduction based on your monthly traffic.
FAQ: Airline CTI and access-based ATO
What is an access-based ATO attack in airlines?
An access-based ATO attack begins with impersonation or session theft, often via reverse proxy tools, rather than direct credential stuffing or brute-force login attempts.
Why are airlines targeted by groups like Scattered Spider?
Airlines offer high-value loyalty assets, operational urgency, and behavioral variability that allow attackers to monetize access quickly while avoiding detection.
How does Evilginx2 enable airline account takeover?
Evilginx2 proxies the legitimate airline login flow and captures session tokens after MFA succeeds, allowing attackers to replay authenticated sessions.
Why do takedown services fail against these attacks?
Takedowns occur after impersonation sites are live and victims have already interacted with them, offering no visibility into compromised sessions or affected users.
How does decoy data improve detection?
Decoy data generates high-confidence signals when attackers interact with it, enabling faster detection, campaign clustering, and early disruption of attacker workflows.
What should airline CTI teams measure instead of fraud loss?
CTI teams should focus on time to detect, time to respond, and attacker dwell time, which directly reflect their ability to disrupt campaigns early.